HSA Releases Draft Guide for Medical Device Cybersecurity
HSA’s Medical Devices Cluster has released a draft on Best Practices Guide for Medical Device Cybersecurity for stakeholder consultation. The document provides recommendations on cybersecurity best practices for medical devices, focusing on both pre-market and post-market stages of the device's Total Product Lifecycle (TPLC).
Target Audience and Consultation Period
This document is targeted for Medical Device Manufacturers and Healthcare providers, and currently available as a draft for consultation. Which opens from 10 March 2025 to 12 May 2025.
Pre-Market Stage Recommendations
The pre-market stage focuses on the development phase, which includes:
- Designing security features (i.e Secure by design)
- Developing risk management strategies
- Conducting thorough security testing
- Preparing user information and documentation
- Developing a post-market cybersecurity plan
- Creating Software Bill of Materials (SBOM)
Post-Market Stage Recommendations
While the post-market stage addresses cybersecurity risks throughout the device’s operational life which is divided into:
- Support Stage
- Limited Support Stage
- End of Support Stage
Purpose and Scope of the Draft Guide
By following the recommended best practices, manufacturers and healthcare providers can work together to enhance the security profile of medical devices, protect patient safety, and maintain the integrity of healthcare systems. However, in the scope of document, HSA mentioned that this document is not intended to provide information on regulatory requirements, but rather offers best practices recommendations and considerations on medical device cybersecurity throughout the TPLC.
General Principles
Under the General Principles section, HSA emphasized that cybersecurity of medical devices is a Shared Responsibility between device manufacturers and healthcare providers. Additionally, Transparency and Communication is also a fundamental principle to ensure the safety and security of medical device. Active participation, timely sharing of information and coordinated vulnerability disclosure between the manufacturers and healthcare providers are the encouraged best practices. Lastly, a medical device should be integrating security measures into the core architecture and design of the device, such Secure by Design principle will result in a more robust and resilient medical devices that are inherently resistance to cyberattacks.
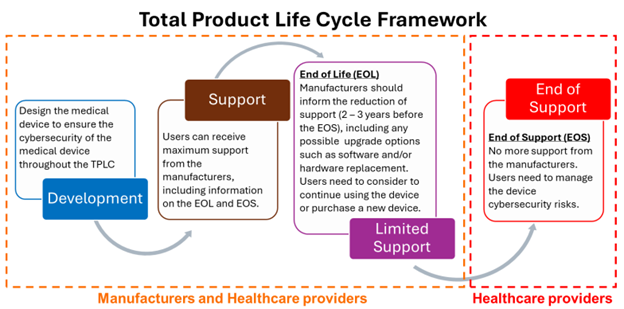
Overview of Total Product Life Cycle Framework (TPLC)
The risk associated with the cybersecurity threats and vulnerabilities need to be considered throughout the Total Product Life Cycle (TPLC) of the medical device. The document also shared an overview of the TPLC stages as seen in Figure 1.
The cybersecurity considerations at each stage of TPLC are discussed more detailed in the following sections of the draft guide document.
Figure 1: Total Product Life Cycle Framework
Pre-market – Development stage
There are specific pre-market elements that should be considered during the development stage to ensure the security of the medical device throughout the TPLC, such as follows:
- Designing Security Features
By incorporating security features into the product design to mitigate potential vulnerabilities and threats. The guide provides several possible design considerations while also sharing two important principles that aim to enhance the security of systems and applications: a) Secure by default, and b) Secure by design.
- Risk Management Strategies
By applying accepted risk management strategies to identify, analyze, assess, and mitigate cybersecurity risks associated with the device.
The guide provides several examples of key strategies to the cybersecurity risk assessment and planning that medical device manufacturers and healthcare provides need to consider in applying accepted risk management strategies. On top of the recommended approach, the cybersecurity risk management process is complementary to and can be integrated as per part of ISO 14971 standard.
- Security Testing
By conducting thorough security testing to identify and address any potential weakness or vulnerabilities in the device's security measures.
The guides provide several common cybersecurity methods that can be considered, such as Vulnerability Assessment, Penetration Testing, Security Audits, Security Code Review, etc. Organizations can adopt the best-fit testing methods or combination of testing methods that is tailored to their specific needs.
- User Information
By providing comprehensive and user-friendly information to guide users on how to operate the device securely and effectively. The guide provides some recommendations of what documentations should be included. Additionally, the guide also explains on the Customer Security Documentation along with the elements that should be considered into the document.
- Post Market Plan
By developing a plan for on-going post-market activities, including monitoring, timely detecting, and addressing any security issues or emerging threats that may arise after the device has entered the market.
The guide provides key considerations for the post market plan, such as 1) Post-market Vigilance, 2) Vulnerability Disclosure, 3) Patching and Updates, 4) Recovery, and 5) Information sharing.
- Software Bill of Materials (SBOM)
SBOM is a list of one or more identified software components, their relationship, and other associated information. SBOM is a comprehensive list of the software components used in building a particular application or system. This includes all the open-source and third-party components, libraries, and dependencies that are utilized in the development of the software.
The guide does not include the selection of SBOM format; however, the guide provides elements to be considered in choosing SBOM format also the use cases demonstrate on how SBOMs play crucial role in enabling organizations to respond in case of cybersecurity incidents.
The guide also provides several use cases to provide examples of the use of SBOM during practical scenarios.
- Additional consideration – Devices with Artificial Intelligence (AI)
The guide explains on additional consideration that should be taken for devices with Artificial Intelligence. To ensure the deployment of a robust and secure AI system, the following key areas to be considered throughout the Ai system development cycle: security, of AI during model design, security during AI development (including AI supply chain security), securing of AI during deployment, and the security of AI during operation and maintenance post-deployment.
Post-market Stages
This section described the three post-market stages in the TPLC of the medical device, which are: Support Stage, Limited Support Stage, and End of Support Stage. The stages reflect different degree of involvement by the medical device manufacturers and users (including the healthcare providers) in terms of the responsibility and the support given for the device.
- Support Stage
During this stage, manufacturers should provide comprehensive cybersecurity support to healthcare providers for the devices in use or deployed. This support should be provided during the following phases: a) Procurement and Installation, b) When device is in use, and c) Transfer of Responsibility (transition from Support Stage to Limited Support stage).
- Limited Support Stage (between End of Life and End of Service)
This is a stage where medical device reached the End of Life and moving forwards the End of Service of its life cycle. End of Life cycle starting when the manufacturer no longer sells the product beyond their useful life, and already notified to the user, while End of Support happens when manufacturer terminates all service support activities and service support does not extend beyond this point.
At this stage, manufacturers should inform the healthcare providers of the reduction of support to Limited Support. Which includes the timeline until EOS, alerts when some parts of the medical device are no longer supported, any available software updates, and any recommended compensating controls.
- End of Support Stage (EOS onwards)
At the EOS stage, full responsibilities are transferred to the healthcare providers where they need to manage the device cybersecurity risks without assistance from the manufacturers. The guide provides recommendations of aspects that should be considered by both manufacturers and healthcare providers to manage this stage smoothly.
Conclusion
The document outlined comprehensive cybersecurity best practices for medical devices, spanning both pre-market and post-market stages of the device’s TPLC. While in conclusion, cybersecurity in medical devices requires shared responsibility and close communication between the manufacturers and healthcare providers.
Call-to-Action
The Consultation period for the draft Best Practices Guide for Medical Device Cybersecurity is from 10 March 2025 to 12 May 2025. Feedback should be uploaded into an online platform established by HSA using the prescribed feedback form before 13 May 2025. Any queries can be emailed to HSA_MD_Info@hsa.gov.sg with "Best Practices Guide for Medical Device Cybersecurity" in the email subject header.
Qualtech Consulting Corporation has supported medical device manufacturers for over 20 years. Whether you’re a local startup or global brand, we empower your devices to enhance lives.
Connect with us today to unlock your medical device potential.