Background of Cyber-Security
Occurrences of data security breach increases along with the frequent use of remote internet-enabled medical devices. Outside connectivity gives bad guys the perfect opportunity to exploit data generated from medical devices for their personal interests. One of the biggest healthcare data breaches that happened in 2016 is when a hospital system was left paralyzed by a hacker, which has incurred huge losses just to recover the internal computer system and finally regain control of the computer after the hack attack. Following this incident, security breach has continued, compromising several hospitals where hackers took advantage of patient data retrieved from remote internet-enabled medical devices. Even if the cybersecurity strategies have been well-developed during those times, it would still not be given much of an importance by most medical device manufacturers.
As awareness on the significance of cybersecurity continues to increase across the healthcare sector, the US FDA has started to update the guidance documents on cybersecurity for medical devices, along with the mandate on duly registered medical device manufacturers to strengthen their cybersecurity measures. Health Administrates from China, Australia and Japan also take initiatives to follow up and regulate relevant guidance documents. The succeeding paragraphs aim to introduce regulation on cybersecurity across Asian countries.
Regulatory Condition in Asia
China:
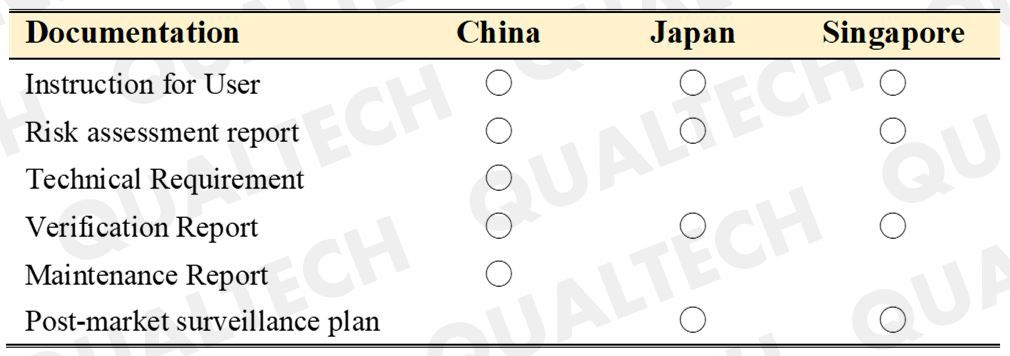
NMPA has issued a guideline in 2017 and has enacted it in the year 2018. It mandates all manufacturers of medical devices with systems having outside connectivity capabilities to strictly adhere to the documentary requirements specific for cybersecurity. The most common technologies incorporated in these types of devices involve the use of "Wi-Fi", "Bluetooth", and "Wire Internet". Applicants would need to provide users and NMPA evaluators a better understanding on the purpose of these outside connectivity, how the various elements in a network are arranged, and how the data moves through them. In addition, the risk assessment, verification reports and maintenance report shall be provided during registration.
In China, Class 2 and Class 3 of medical devices would need to undergo type-testing prior to registration. With the implementation of this guideline, the assessment of the medical device's communication functionalities hall also be carried out during the type testing.
Japan:
PMDA has issued the "Guidance for Cybersecurity of Medical Device" in 2018. This guidance applies to all classes of medical device, covering all medical device or medical device accessories that can communicate and interact with each other. Examples include devices that can be connected to other devices or instruments via USB cable, internet, Bluetooth, or in some other ways. PMDA stresses out the need for risk assessment of cybersecurity and other related security control measures. Manufacturers are requested to include relevant information regarding the suitable network environment on the user manual. Moreover, manufacturers and distributors should assume responsibilities in setting up post market cybersecurity policies (e.g., technical support, software maintenance) appropriate to their devices.
Singapore:
HSA has not issued a solitary guideline for the cybersecurity, however, there are some related requirements listed under the major regulations for General Medical Devices and IVDs –“GN-17: Guidance on Preparation of a Product Registration Submission for General Medical Devices using the ASEAN CSDT” and “GN-18 Guidance on Preparation of a Product Registration Submission for In Vitro Diagnostic Medical Devices using the ASEAN CSDT”.
The scope of Cybersecurity requirement applies for all devices covers that are either wireless-enabled, internet-connected or network-connected. Manufacturers are expected to meet cybersecurity regulations by submitting relevant documents such as “Cybersecurity vulnerabilities and Risk assessment”, “Cybersecurity control measures” and “On-going plans, processes or mechanisms for surveillance, timely detection and management of the cybersecurity related threats during the useful life of the device, especially when a breach has been detected”.
HSA also expects manufacturers to incorporate the post-market surveillance plan into the product life cycle in order to anticipate security threats from the internet.
Table. The Comparison of Submission Document in Different Area
How to Face It?
Most medical devices with embedded programs have undergone series of cybersecurity testing and validation from the point of its development phase. These tests come in variety - be it accessibility tests, USB port connectivity test, and something similar whichever comes to mind. In fact, even installation of Antivirus Software requires one cybersecurity test we call compliance test! Results of these tests are commonly included along with other Software Test Reports. However, results generated from these types of tests prove insufficient to persuade evaluators that your device is invulnerable to security breach. One strong evidence of cybersecurity is the conduction of 'penetration test', also referred to as 'white box', 'gray box' or 'black box'.
The manufacturer should understand the potential risks associated to cybersecurity related to the medical device’s functionality. The approaches to cyber-attack have evolved very quickly, hence, the manufacturer shall try to stay ahead of the game by evaluating all possible vulnerabilities pertinent to network security and update control measures annually. Just as software documentation, all updates shall be incorporated into the traceability report. Providing traceability reports also gives authorities an impression that cybersecurity issues are properly addressed by the company.
Conclusion
Internationally recognized standards for Cybersecurity such as IEC 80001 are made available for manufacturers to serve as a guide in establishing effective and feasible systems for cybersecurity. These set of standards shall be taken into consideration in the design stage of the product life cycle. For some devices that are already available in the market, it would be better to strengthen security protection measures to prevent potential risks from outside evaders. These actions yield benefits to every stakeholder.
While it is expected that several Notice Documents on Cybersecurity will be published every now and then, it would be a good practice for clients to build up feasible solutions within their companies as an initiative to stay ahead of these issues. With thorough preparation, smooth registration process and access to Asian markets most likely await next generation products.
Reference:
- China: Guidance of Cybersecurity in Medical Device
- Japan: Guidance of Cybersecurity in Medical Device
- Australia: Draft Guidance of Medical device cyber security
- United State: Content of Premarket Submissions for Management of Cybersecurity in Medical Devices
- Singapore: GN-17 Guidance on Preparation of a Product Registration Submission for General Medical Devices using the ASEAN CSDT